Survey the workplace and look at what could reasonably be expected to cause harm. Identify all tasks being performed.

Check manufacturers or suppliers instructions or data sheets for any obvious hazards.
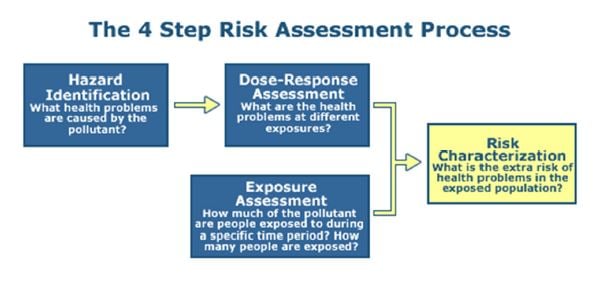
Four steps of risk assessment. A risk assessment is performed in 5 steps or stages. Survey the workplace and look at what could reasonably be expected to cause harm. Identify common workplace hazards.
Check manufacturers or suppliers instructions or data sheets for any obvious hazards. Review previous accident and near-miss reports. Efficiently identify hazards by using checklists.
The risk library provides the framework for the risk assessment process. It summarizes and defines in a common repository those risks to which the company is exposed. The library helps to facilitate discussions of risks and their definitions and it promotes both consistency and a culture of risk awareness.
To help streamline the process at Gen Re our risk library is broken into four. After examining all parts of the four-factor breach risk assessment you must draw a conclusion in good faith about the overall level of risk. Based on the nature of the PHI the unauthorized person receiving it the acquisition or use of the PHI and the mitigation steps taken is it likely or unlikely that the PHI was compromised.
Again if the risk is greater than low you must notify all. Risk assessments can be daunting but weve simplified the ISO 27001 risk assessment process into seven steps. Define your risk assessment methodology.
There is no set ISO 27001 risk assessment procedure. Instead you should tailor your approach to the needs of your organisation. To do this you need to review certain things.
First you should look at your organisations context. A human health risk assessment includes four steps which begin with planning. Planning - Planning and Scoping process EPA begins a human health risk assessment by planning the overall approach with dialogue between the risk managers risk assessors and other interested parties or stakeholders.
Members of the team. Identify risk management goals and options. The risk assessment process in 4 steps.
There are many ways to respond to risk and each identified risk can be addressed in one of four ways. This risk is tolerable and our company can surmount it Reducing the risk. This risk is a little steep and we should take steps toward minimization ahead of time.
This risk could be shouldered by multiple teams. This tool allows those working in low-risk office-based environments to do their risk assessment quickly and easily. The Health and Safety Executive has developed this tool in consultation with Local Government Regulation and supports the approach for these businesses.
It enables you to produce a tailored assessment by selecting the relevant hazards and thinking about how you control them. The Four Critical Steps. By Safety Management Group Like fire chemicals are very useful for a broad variety of functions.
But just like fire many chemicals are inherently hazardous or even deadly when theyre not used in a properly controlled manner or when accidents occur. Thats an important fact to remember because chemicals are used to some degree at nearly every. The four key components.
An IT risk assessment involves four key components. Well discuss how to assess each one in a moment but heres a brief definition of each. Threat A threat is any event that could harm an organizations people or assets.
Examples include natural disasters website failures and corporate espionage. Five steps to risk assessment can be followed to ensure that your risk assessment is carried out correctly these five steps are. Decide who might be harmed and how.
Evaluate the risks and decide on control measures. Record your findings and implement them. Review your assessment and update if necessary.
In order to identify hazards you. When a Fall Occurs Four steps to take in response to a fall. AJN American Journal of Nursing.
November 2007 Volume 107 Number 11 page - Free Authors. Hendrich Ann MSN RN FAAN. Article Content Step one.
When a patient falls dont assume that no injury has occurred-this can be a. Risk analysis is about understanding the risks in the risk register. To analyze legal risks begin with an assessment of controls.
Risk controls can take a variety of forms depending on the risk the industry and the organization. For example to manage a contract risk an organization might use a requirements tracking system to ensure that individual obligations are satisfied. Occupational risk assessment is a method for estimating health risks from exposure to various levels of a workplace hazard.
Understanding how much exposure to a hazard poses health risks to workers is important to appropriately eliminate control and reduce those risks. The aim of a risk assessment is to answer three basic questions. Risk assessment then is a systematic process of evaluating the potential risks that may be involved in a projected activity or undertaking.
In other words risk assessment involves identifying analyzing and evaluating risks first in order to best determine the mitigation required. Lets break down the three components of risk assessments. Look critically at your.
Here are some steps for writing a construction risk assessment with iAuditor. Provide all necessary details such as company or site name people involved date and time and location. Identify all tasks being performed.
Determine the hazards associated with the tasks performed by the workers. Hazards can either be working at heights electrical tasks use of heavy types of machinery or lockout. Radar contains risk data based on independent and reputable sources that assess risks in the four SMETA pillars and 14 risk topics.
Radar can help you carry out the key stages of a risk assessment within the human rights due diligence process helping to inform your next steps. Validating whether the risks are occurring in practice and developing action plans to manage and mitigate them. Testing would typically include an annual Tabletop Test andor Walk-Through Test of all four individual EPP plans testing multiple scenarios for threats that you identify as higher-risk to your organization.
Be sure to test the scenarios that you believe to be the highest risk to your organization most frequently and the scenarios you dont believe to be that probably less frequently. The core of the risk assessment process is based on the four steps shown in Figure 2. These four steps are followed in each of the three levels of risk assessment but with increasing depth and different types of analysis.
Table 2 shows a general overview of these four steps for the three levels of assessment. These are discussed in further detail in each guidance document see below. The executive summary should include four basic elements.
Purpose of analysis. Lets go through each section one by one. You will want to start the executive summary by describing why you were hired to perform this assessment.
This is a great opportunity for you to demonstrate that you understand the. There are some fundamental steps needed to achieve successful risk management for projects using the risk assessment matrix. Risk Identification Defining and identifying the risks associated with a project is the initial phase in risk control.
The result of the risk assessment is a prioritized list of hazards which ensures that controls are first identified for the most serious threat to mission or task accomplishment. Combine the severity with the probability to determine the risk assessment code RAC or level of risk for each hazard expressed as a single Arabic number. Although not required the use of a matrix such as the one.
Historically discussions around risk assessment have focused on how to identify factors that are predictive of reoffending step 1 and how to combine them into a single scale or risk score steps 2 and 3. Risk assessment researchers strive to identify relevant and appropriate predictors and improve upon statistical models of risk prediction. Some of the latest instruments incorporate case.
The fraud risk assessment should address four key areas. Asset misappropriation financial and non-financial reporting regulatory compliance areas and illegal acts. In general cash inventory and company assets are subject to misappropriation and must be examined for potential skimming larceny and fraudulent disbursements.
Asset misappropriation is also more than. A Risk Assessment is an examination of what could cause harm on a particular shoot or at a specific location so that the production company producer can decide whether adequate control measures are in place to prevent harm. What does a risk assesment look like.
A simple one say for evaluating a single hazard like using a tower scaffold as a camera platform can be on a single sheet of. Risk assessment is viewed as a barrier to day-to-day business activities. A realization of the flaws inherent in the process as discussed in the above four steps combined with lack of accountability leads to lackluster implementation.
More often the risk findings are not acted upon at all. Challenges abound but so do remedies and opportunities. What requires is a well-intentioned change.